A major threat to healthcare organisations
Insecure, misconfigured and under-protected remote desktop services are a major vulnerability. This attack vector is simple to find, easy to access and operate, very simple to exploit and can be the initial entry to a chain of devastating actions by a threat actor to take down your systems.
This screenshot is of a single, exposed live system that our team of volunteers has obtained (amongst a range of others) from live vulnerable systems on the internet:
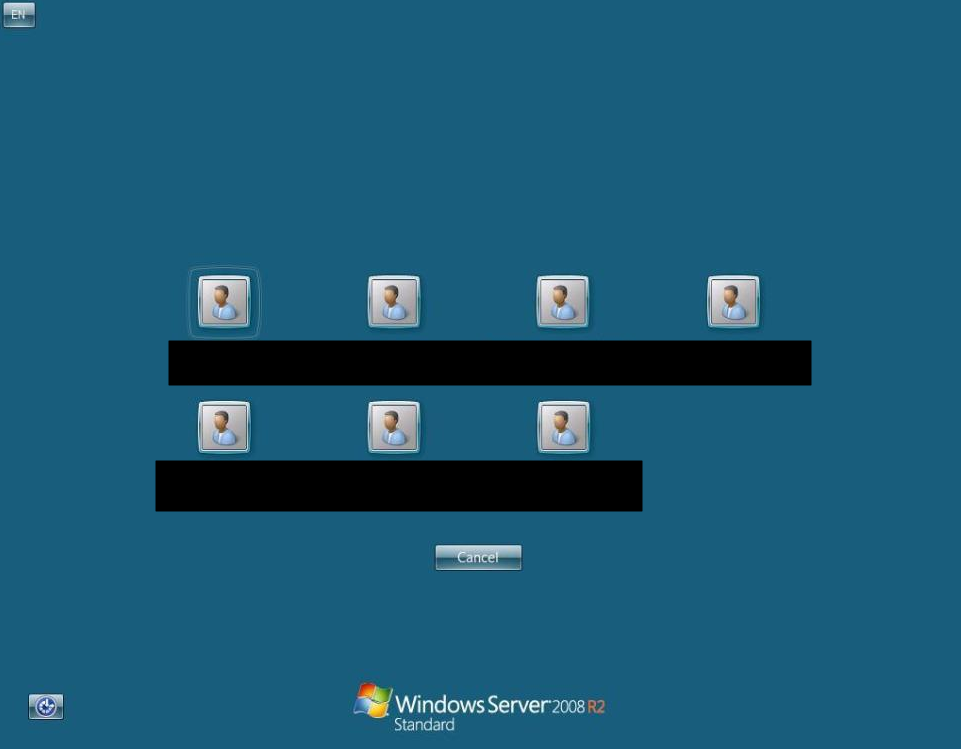
You can see here that not only are we able to enumerate valid usernames, but we are also able to enumerate and identify the operating system (in this case it’s an out-of-support Windows Server 2008 R2 Standard Edition Server).
It’s important to also recognise that it’s not just RDP (Remote Desktop Protocol) services, there are a ton of systems which have remote code execution or authentication bypass vulnerabilities which will enable threat actors (cybercriminals) to potentially own your systems and data! Examples of these include vulnerabilities in systems such as PULSE VPN, CITRIX NETSCALER and RDP:
Common Ransomware Phases
Phase 1 – Recon
Threat actors identify exposed RDP services. They identify if NLA (Network Level Authentication) is disabled (if so, this provides them username enumeration to increase the likelihood of success). It should be noted that threat actors also buy and sell access credentials on marketplaces, so it some cases they skip straight to initial access.
Phase 2 – Exploitation
Threat actors obtain breached credential data and leverage this amongst other techniques (such as brute force) to attack the exposed services. These methods include:
- Valid credentials
- Credential stuffing
- RDP exploits (such as Bluekeep)
- Brute force
Phase 3 – Initial Access
Once a valid connection is made, the threat actor now has an initial foothold. From here they will attempt to do the following:
- Harvest local access and data sources to elevate privileges (often they will run mimikatz)
- Check web browser password caches
- Check for clear text credentials stored in files
- Check saved credentials in RDP sessions (Windows Credential Manager)
- Enumerate the network using legitimate network scanning tools
- Prepare ransomware payloads
- Some ransomware requires communication with a command and control (C2) server; however, some ransomware such as REvil can be executed with a custom binary which does not require server communication.
Phase 4 – Lateral Movement
The threat actors will attempt to move to other nodes on your network to increase their position. In some cases, they will also establish persistence and several backdoors in case one access method is discovered and removed. You will often see them dump legitimate tools to scan networks to attempt to evade detection.
Phase 5 – Actions on Target
Once all resources have been exhausted, the threat actor will execute (run) the payloads to encrypt your data.
Phase 6 – Victim Contact and Payment
Once the servers and data have been encrypted, the ransomware operator will either wait for contact or will establish contact. This will usually be conducted using throwaway (burner) email accounts, etc. Most ransomware leaves a ransom note with details as to how to establish contact and how to arrange payment to the attacker.
Identify, Protect, Detect, Respond and Recover
There are a range of actions that can be taken to not only reduce the risk of incident occurrence but also to help mitigate the impact. The range of options are wide, so we’ve gone into the common ones:
- Ensure you have an ‘offline’ backup
- This may be in the form of a network-based backup that is NOT domain joined and is significantly isolated. Ideally, you want a copy of these backups shipped offsite as well.
- Ensure you have an incident response plan
- Ensure that it is tested (alongside restoration tests from backup services)
- Ensure you have NLA enabled. This will in some cases stop exploits (e.g. Bluekeep) or will significantly increase the complexity of the attack required.
- Use IP whitelists and/or “just in time” access
- Use VPNs and Secure Gateway services
- Ensure you have account lockout policies configured
- Implement proactive security monitoring
- Implement Multi-Factor Authentication (MFA)
- Use hardened configurations, jump boxes, limit standard user accounts
- Ensure systems are patched and maintained in line with vendor support
- Ensure logging configurations are set appropriately
- Deploy sysmon, if suitable
- Deploy EDR (Endpoint Detection and Response), if safe to do so
Alongside our guidance, please review the NCSC guidance on ransomware defence and response:
https://www.ncsc.gov.uk/guidance/mitigating-malware-and-ransomware-attacks
In short, practise good systems’ management. You can harden your attack surface with some very simple changes and you can make it insanely stronger with a bit more effort!
Summary
The risks that exposed RDP services present are huge. It’s estimated that ~80-85% of ransomware incidents use this vector as an initial foothold. One of our founders (Daniel Card) has personal experience responding to ransomware and in the last ~6 months, 100% of his responses have been due to exposed RDP.
There are clearly requirements to enable remote administration, but what we are seeing is many servers being exposed with high risk configurations in the healthcare sector. It’s imperative during this time that healthcare providers and IT service providers ensure their internet-facing assets are not exposed to unnecessary risks. We hope this article is useful, but if you need further guidance or support, please get in touch. We have a large group of volunteers who are experienced cyber security professionals and skilled in detection, protection and response services.
If you need support please visit this url : http://cyberv19.org.uk/service-request/
and one of our team will be in contact to help!
Stay safe, stay secure!
References
https://www.bleepingcomputer.com/news/security/chubb-cyber-insurer-allegedly-hit-by-maze-ransomware-attack/
https://www.coveware.com/blog/2019/1/21/covewares-2018-q4-ransomware-marketplace-report






